The Spanning Tree Protocol (STP) Attacks (Layer 2) + Understand the Basics

Spanning Tree Protocol (TP) is a network layer protocol that aids in the creation of a logical loop-free topology for ethernet networks. With the passage of time, several improved implementations of STP entered the industry, introducing new changes to the protocol:
- 802.1D / STP (Original STP)
- PVST+ is a combination of PVST and PVST (Cisco improvements of STP, adding a per VLAN feature)
- 802.1W / RSTP (Improved STP with much faster convergence)
- Rapid PVST+ (Cisco improvement of RSTP, adding per VLAN feature)
ON THIS PAGE: The Spanning Tree Protocol (STP) Attacks (Layer 2) + Understand the Basics
-
STP Varieties
-
Understanding the Differences Between 802.1D and 802.1Q Common STP
-
Recognizing 802.1w Rapid STP
-
Understanding Multiple STP in 802.1s
-
More Information about STP Operation
-
Timers for the Entire Network
-
STP and BroadCast Storm
-
Broadcast Storm (Scenario 1)
-
Scenario 2: Packets that are duplicates
-
What really is the issue here? Without reading any more, would you make a guess?
-
In STP, which port should be blocked?
-
Bridge of the Roots
-
Bridge that has been designated
-
Bridge Alternate
-
Bridge as a backup
-
Disable
-
Portforwarding
-
Port of learning
-
Port of Listening
-
Discarding port
-
Operation of the Spanning Tree Protocol
-
Identifying the most cost-effective path to the Root Bridge
STP Varieties[ps2id id='STP Varieties' target=''/]
STP comes in a variety of forms today, either as IEEE specifications (802.1Q Common STP, 802.1w Rapid STP, and 802.1s Multiple STP) or as private vendor additions. They all work in the same way; the only difference is the time it takes to compute an alternative topology in the event of a connection loss. Proper STP functioning is essential, but it is also very fragile, as this chapter will show.
Understanding the Differences Between 802.1D and 802.1Q Common STP[ps2id id='Understanding the Differences Between 802.1D and 802.1Q Common STP' target=''/]
The IEEE 802.1D specification, first published in 1993, provides a method and a protocol for creating a loop-free topology in a Layer 2 network. (There was no such thing as a VLAN at the time.) The program also guarantees that automated reconfiguration occurs in the event of a connection or device failure. By today's standards, the protocol converges slowly: up to 50 seconds (sec) using the default protocol clocks. The 802.1Q specification subsequently supplemented the 802.1D specification by defining VLANs, but it fell short of suggesting a method to operate a separate spanning-tree instance per VLAN, which many switch manufacturers naturally did using private modifications to the 802.1D/Q standards.
Recognizing 802.1w Rapid STP[ps2id id='Recognizing 802.1w Rapid STP' target=''/]
The 802.1w (Rapid Reconfiguration of Spanning Tree) standard, which was included in the 2004 version of the 802.1D standard, made substantial improvements, particularly in terms of convergence rates. According to the IEEE, the following are the reasons behind 802.1w:
The aim to create a better mode of bridge operation that, while maintaining the plug-and-play advantages of spanning tree, eliminates some of the less desired features of current STP (most notably, the considerable time it takes to reconfigure and restore service on link failure/restoration).
The discovery that, although modest increases in spanning-tree performance may be obtained by modifying the current default parameter settings, substantial modifications to the way the spanning-tree algorithm works are required to make considerable gains.
The discovery that it is feasible to make enhancements to the operation of spanning trees that take use of the growing popularity of structured wiring methods while still being compatible with equipment based on the original spanning-tree algorithm.
The bottom line is that 802.1w converges in less than a second most of the time. All Cisco switches running the most current software releases set 802.1w as the default STP protocol.
Understanding Multiple STP in 802.1s[ps2id id='Understanding Multiple STP in 802.1s' target=''/]
The IEEE 802.1s provides the ability for bridges to utilize multiple spanning trees, allowing traffic from various VLANs to travel via possibly diverse routes inside the virtual bridged LAN. The improved scalability it offers in large bridged networks is the main motivation behind the creation of 802.1s. Indeed, rather of operating a single spanning-tree instance per VLAN, an arbitrary number of VLANs may be mapped to a spanning-tree instance.
The loop-breaking technique is now executed at the instance level rather than at the VLAN level. You may, for example, map a thousand VLANs to a single spanning-tree instance using 802.1s. This implies that all of these VLANs have the same logical topology (blocked port blocks for all of them), but the savings in CPU cycles is substantial.
More Information about STP Operation[ps2id id='More Information about STP Operation' target=''/]
To comprehend the assaults that a hacker is likely to launch against STP, network managers must first acquire a thorough knowledge of the technology's inner workings. The protocol creates a tree-like loop-free topology. A root bridge is located at the base of the tree; an election procedure is used to decide which bridge becomes the root.
The switch with the lowest bridge ID (a 16-bit user-assigned priority and the switch's MAC address) wins. The root-bridge election procedure starts with each switch in the domain believing it is the root and asserting it across the network using Bridge Protocol Data Units (BPDU).
In the case of IEEE STP (01-80-C2-00-00-00), BPDUs are Layer 2 packets broadcast to a well-known MAC address; in other instances, BPDUs are vendor-assigned addresses. When a bridge receives a BPDU from a neighbor, it compares the sender's bridge ID against its own in order to determine which switch has the lowest ID.
Only the switch with the lowest ID continues to generate BPDUs, and the procedure is repeated until a single switch wins the specified root-bridge election. STP gives network ports responsibilities and functions. Every nonroot bridge has one root port, which connects to the root bridge.
STP constructs its loop-free tree using a path cost–based approach. Every port is assigned a port fee; most switches may autoassign charges depending on connection speed.
The cost of a port is proportional to its bandwidth. When a port gets a BPDU, the port's route cost is added to the BPDU's path cost. The root transmits BPDUs with a route cost of zero, and the cost rises as the network diameter grows. When two BPDUs arrive on a switch as a result of duplicated network connections, the one with the greater cost is logically disabled—it is placed in blocked mode.
The designated bridge is the bridge that is in charge of forwarding packets on a certain segment. The network converges after a time, which may range from less than a second to just under a minute depending on the STP flavor, and a single-rooted loop-free tree is created. Before a port may be used for forwarding, it must first go through the following stages:
- Disabled. The port is electrically inactive and does not transmit or receive data. When activated, the port advances to the next state (blocking).
- Blocking. Except for BPDUs, this function discards all data frames.
- Listening. To construct the loop-free tree, switches listen for BPDUs. Data packets are not routed (15 sec by default with 802.1D timers).
- Learning. Data frames are not forwarded; forwarding tables are constructed using the source MAC addresses of data packets.
- Forwarding. Data transmission. The port is fully functioning at this time.
NOTE: Although this chapter provides a comprehensive picture of STP's inner workings, if you want a more extensive understanding, we suggest that you look at the reference material accessible online2. STP network-wide timers keep the network stable once it has converged. (A VLAN may be part of a network.)
Timers for the Entire Network[ps2id id='Timers for the Entire Network' target=''/]
There are many STP timers:
- Hello. Time elapsed between each BPDU transmitted on a port. This time is set to 2 seconds by default, but you may change it to anything between 1 and 10 seconds.
- Delay in the future. The amount of time spent listening and learning. This duration is set to 15 seconds by default, but you may change it to anything between 4 and 30 seconds.
- Maximum age. The maximum amount of time before a bridge port stores its configuration BPDU information. This duration is set to 20 seconds by default, but you may change it to anything between 6 and 40 seconds.
These three parameters are included in each configuration BPDU. Furthermore, each BPDU configuration includes a time-related option known as the message age. The message age is not a constant. The message age specifies the amount of time that has elapsed since the BPDU was created by the root bridge.
The root bridge transmits all of its BPDUs with a message age of zero, and all subsequent switches add one to this number. When you get a BPDU, this value effectively includes information about how distant you are from the root bridge.
Read More: Google I/O 2021 Highlights: Assistant, Android 12, and ‘Material NEXT’
Bridges in 802.1D have no clue if their BPDUs are heard by adjacent switches. For example, the root bridge cannot be certain that everyone recognizes its existence since the protocol makes no provision for this. The protocol merely depends on timers (as previously described) to ensure that BPDUs are sent to every bridge in the network. An 802.1D BPDU is shown in Table 3-1.
STP and BroadCast Storm[ps2id id='STP and BroadCast Storm' target=''/]
Cisco has made a lot of progress in this region, as you can see. Let's start from the beginning and examine why STP was needed in the first place.
Before we get into why STP is required, let's have a look at how layer 2 works when it needs to find the address of a specific host.
When a switch receives a packet but does not have the destination node's MAC address in its table, it broadcasts the message to all nodes except the one it is receiving from.
Broadcast Storm (Scenario 1)[ps2id id='Broadcast Storm (Scenario 1)' target=''/]
Take a peek at the following scenario:
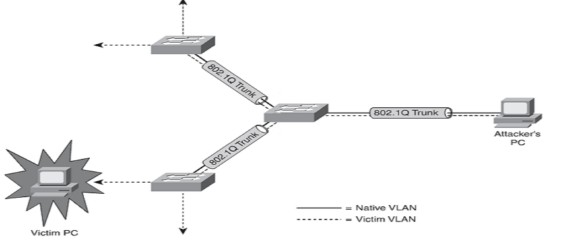
Assume a network of three switches, as seen in the diagram. Many of the switches are linked together. Switch B sends a broadcast, which is received by Switch A and Switch C. They are unable to locate the address and must broadcast the alert again.
Switch B receives the rebroadcast alert from Switch A and Switch C for the second time. Switch B considers the broadcast to be a new broadcast and repeats the same messages that had already been broadcast. A televised storm occurs in this manner. It will proceed until either the ports or the switch/switches malfunction.
https://www.techguruhub.net/2021/05/spanning-tree-protocol-stp-in-a-nutsell-configuration-explained/If you glance at the description once more, you'll see why STP was created in the first place.
Scenario 2: Packets that are duplicates[ps2id id='Scenario 2: Packets that are duplicates' target=''/]
Consider the same network design as the one described in the previous scenario. There's a twist in this tale. Switch C has now established a link to the destination host that Switch B has been searching for. So, what's next?
Switch B will start broadcasting once more. Switch C and Switch A are both reached through the broadcast. Switch C examines the packet and forwards it to the target host.
Switch A, on the other hand, searched the table and was unable to locate the destination host. As a result, it broadcasted the alert as well, and Switch C got the same packet twice. As a result, it examines the packet and redelivers it to the destination host.
What really is the issue here? Without reading any more, would you make a guess?[ps2id id='What really is the issue here? Without reading any more, would you make a guess?' target=''/]
The most serious issue here is repeat distribution and bandwidth waste.
Let us now look for an answer to scenario 2. To avoid packet replication, one of the best and simplest alternatives is to disconnect Switch B from Switch C. Since, if the destination host is not included in Switch A's catalogue, the packet will be broadcast to Switch C. It now seems to be more like this:

Despite the fact that we have discovered the answer, we are also undecided as to whether blocking the connection between B and C or the link between Switch B and A was more valuable. Let's take a closer look at each of these points.
In STP, which port should be blocked?[ps2id id='In STP, which port should be blocked?' target=''/]
STP follows a set of basic steps that assist it in addressing a variety of problems, including determining which ports to block. But first, let's go through some words that may be useful to you:
Bridge of the Roots[ps2id id='Bridge of the Roots' target=''/]
Root Bridge is the key Switch or Bridge in a Graph where separate nodes reflect all other bridges, much as a "Root" in a tree layout. The spanning tree topology is regulated by the root bridge.
Bridge that has been designated[ps2id id='Bridge that has been designated' target=''/]
The assigned bridge is the switch that is nearest to the Root Bridge, and it is via this switch that the frames are forwarded to the Root Bridge.
Bridge Alternate[ps2id id='Bridge Alternate' target=''/]
This is a distinct direction to the Root Switch than the one that requires the use of the Root Bridge.
Bridge as a backup[ps2id id='Bridge as a backup' target=''/]
This is a backup route to a segment, but another path would be accessible.
Disable[ps2id id='Disable' target=''/]
Ports that have been removed.
The following are the various states in which a switch port may be at any given time:
Portforwarding[ps2id id='Portforwarding' target=''/]
This is a fully functional dock.
Port of learning[ps2id id='port of learning' target=''/]
A port that learns the MAC addresses rather than forwarding frames.
Port of Listening[ps2id id='Port of Listening' target=''/]
This is a port that isn't routing frames or knowing MAC addresses.
Discarding port[ps2id id='Discarding port' target=''/]
A port that does not send or receive results.
Let's have a look at how STP works and how it determines which Switch, Bridge, and Port must be in which state:
- In the first move, a root bridge is chosen (how root Bridge is elected has been covered later in this article).
- The root bridge's ports are switched to forwarding mode.
- Root Port refers to the ports on the assigned bridges that link to the Root Bridge.
- On a specified Bridge, the remaining ties chose designated ports.
- The remaining ports have been put in a blocking zone.
Here's a stunning example from Wikipedia.
Root Port (STP RP)
DP stands for Designated Port.
Blocked Port (BP)
While the overall procedure seems to be easy, the operating method behind the scenes is very complicated. The algorithm takes longer to position anything in its proper place as the network becomes wider.

Operation of the Spanning Tree Protocol[ps2id id='Operation of the Spanning Tree Protocol' target=''/]
The tasks that follow take place.
The Root Bridge's Position
Let's start from the beginning of this situation. Assume that the network is being built from the ground up. When any of the switches in the network are turned on, they all pretend to be the root bridge.
To verify the argument, both switches must use BPDUs to broadcast their Bridge ID (BID) (Bridge Protocol Data Units). The total size of the Bridge ID is 8 bytes, with 2 bytes reserved for the Bridge Priority and the remaining 6 bytes reserved for the MAC address.
Bridge ID is made up of a MAC address and a Bridge priority. Behind the scenes, the BID is a concatenation of Bridge priority and the Switch/ Bridge's MAC address. Each bridge will be assigned a bridge ID of 32768 by chance, and each bridge ID will be in multiples of 4096.
What factors go into determining the Root Bridge?
Following the broadcast of each Bridge's Bridge ID, the Bridge with the lowest BID becomes the Root Bridge. If the Bridge priority is the same in both scenarios, the Mac address with the lowest priority wins.
Consider the following scenario:
Assume there is a connection between two bridges with the following BIDs:
Bridge A: 32768.df56.6765.7876 and,
Bridge B: 32768.df56.6765.7875
Here's a query for you: one of the bridges would become the root bridge in this situation? You were correct if you assumed Bridge B was the response.
Graphical Illustration:
Let's see how both of these switches reacts to the BPDUs:
As previously said, as soon as all of the switches are powered up, they all advertise that they are the root bridge by sending their Bridge ID in a hello packet.
1st switch:
Switch 1 matches the Bridge ID values as it collects hello BPDUs from Switch 2 and Switch 3. Switch 1 has the lowest BID in this case. As a result, Switch 1 ignores the hello packets from the other Switches and continues to advertise itself as the Root Bridge.
2nd switch:
Switch 2 receives Hello BPDUs from all Switches, Switch 1 and Switch 3, in this case. Let's have a look at how Switch 2 responds to both BPDUs.
As Switch 2 receives a packet from Switch 1, it matches the BID values and determines that Switch 1's hello packet BPDU supersedes the BID. As a result, Switch 2's BID is changed to Switch 1's. It will equate the values as it collects the BPDU from Switch 3 and will continue to drop the BPDUs from Switch 3.
3rd switch:
Assume Switch 3 is the first to receive the BPDU from Switch 2. As a result, it switches its Offer to Switch 2. However, as it gets another BPDU from Switch 1, it switches it back to Switch 1.
At this stage, all of the switches have obtained each other's BPDUs and determined that Switch 1 has the lowest BID value and is therefore the best choice to serve as the network's Root Bridge.
Switch 2 and Switch 3 begin grouping their respective connections into Root Ports and Designated Ports until the Root bridge has been determined, as discussed at the beginning of the post.
However, electing the Root Bridge is just the first step. This is just the start. The game continues as follows: –
Identifying the most cost-effective path to the Root Bridge[ps2id id='Identifying the most cost-effective path to the Root Bridge' target=''/]
If you're familiar with graph theory's spanning tree, you'll understand why we're concerned about finding the cheapest path to the root bridge.
A spanning tree is a subset of Network in graph theory. The spanning tree helps you to cover all of the graph's vertices with the fewest amount of edges available. As a result, a spanning tree does not have a loop and, most importantly, it cannot be disconnected.
The Spanning Tree Protocol takes advantage of the fact that, like the Spanning Tree in graph theory, this network protocol can determine the cheapest route from every node to the root bridge.
So, after the Root Bridge has been determined, each node begins determining the lowest cost to the Root Bridge in order to maximise the entire network.
The Root Bridge sends the BPDUs flow to all of the other Switches as the first move. The root cost is calculated by including the costs of each section on the route that a BPDU packet travelled from the Root Bridge to the node.The cost of a segment is often determined by the connection speed of the segment in question.
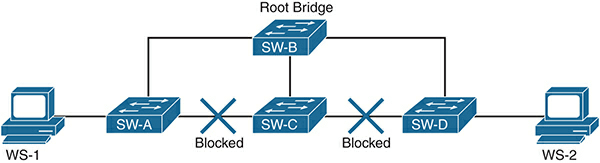
These connection costs may also lead to interesting circumstances involving the lowest-cost route to the Root Bridge. Take a look at the following image: –

In the image above, can you figure out what the Root Port for Switch 3 is?
While it seems that Switch 3 is directly linked to the Root Bridge and that this should be its direction, when the connection cost is calculated, the following flow is the better for Switch 3 to submit data to the Root Bridge.
Root Bridge -> Switch 2 -> Switch 4 -> switch 3
Will you figure out why? Here are the prices, as seen in the graph above:
Since it is a 10 Mbps connection, Switch 3 to Root Bridge is directly 100. However, if we quantify the direction as mentioned above, we get (19+19 +4 = 42).
As a result, in each non-root Bridge, the port that receives the BPDU with the lowest cost becomes the bridge's root port.
The Designated port is then assigned to all connections linked to the Root port on the opposite side. Additionally, the blocked ports are identified. Once all has been labelled and fixed, the network would have a completely optimised spanning tree protocol.
There may be additional circumstances. In the case of a big network, the connection expense would be tied. The network expense is measured as part of Advanced STP in this scenario. Advanced STP also discusses what occurs if a connection goes down.
Read More: Learn how to update your IP address to troubleshoot your internet link or secure your anonymity.
https://www.techguruhub.net/spanning-tree-protocol-stp-attacks/?feed_id=110881&_unique_id=64048dd10375c
Comments
Post a Comment