What Is The Difference Between TCP/IP And The OSI Seven-Layer Network Model?

The OSI and TCP/IP networking models are compared and contrasted.
The Internet is made possible through network-to-network links. The "network layer" of the Internet communications process is where these connections are made by passing data packets back and forth across various networks. The network layer is layer 3 in the seven-layer OSI model (shown below). The Internet Protocol (IP), along with many additional protocols for routing, testing, and encryption, is one of the primary protocols used at this layer.
ON THIS PAGE: What Is The Difference Between TCP/IP And The OSI Seven-Layer Network Model?
-
What exactly is a network?
-
What takes place at the network layer?
-
What exactly is a packet?
-
The OSI Model (Open Systems Initiative)
-
TCP/IP (Transmission Control Protocol/Internet Protocol)
-
What are the benefits of using the OSI model?
-
The OSI model's drawbacks
-
In conclusion
-
Bibliography
Assume Bob and Alice are both connected to the same local area network (LAN), and Bob wishes to send a message to Alice. Because Bob and Alice are on the same network, he may transmit it straight to her computer across the network. If, on the other hand, Alice is on a separate LAN many miles away, Bob's message must be addressed and transmitted to Alice's network before it can reach her computer, which is a network layer operation.
What exactly is a network?[ps2id id='What exactly is a network?' target=''/]
A network is a collection of two or more computer devices that are linked together. Typically, all network devices are linked to a central hub, such as a router. Subnetworks, or smaller subdivisions of the network, may also exist on a network. Subnetworking is the method through which extremely large networks, such as those offered by ISPs, can handle thousands of IP addresses and linked devices.
Consider the Internet to be a network of networks: computers are linked together inside networks, and these networks are linked to other networks. This allows these computers to communicate with other computers both nearby and far away.
What takes place at the network layer?[ps2id id='What takes place at the network layer?' target=''/]
The network layer is where everything that has to do with inter-network connections happens. This involves configuring data packet routes, determining if a server on another network is operational, and addressing and receiving IP packets from other networks. Because the overwhelming bulk of Internet data is transmitted via IP, this final step is probably the most essential.
What exactly is a packet?[ps2id id='What exactly is a packet?' target=''/]
All data transmitted over the Internet is divided into smaller pieces known as "packets." When Bob sends a message to Alice, for example, it is broken down into smaller bits and then reassembled on Alice's computer. A packet is made up of two parts: the header, which includes information about the packet, and the body, which contains the actual data being delivered.
When a packet is transmitted over the Internet, networking software attaches a header to it at the network layer, and networking software on the receiving end may use the header to determine how to handle the packet.
Each packet's header includes information about its content, source, and destination (somewhat like stamping an envelope with a destination and return address). An IP header, for example, includes the destination IP address of each packet, the overall size of the packet, whether or not the packet was fractured (split up into even smaller pieces) in transit, and a count of how many networks the packet has traversed.
Many data transmissions today take the form of packets of data travelling through one or more networks, whether wired or wireless. However, before these networks will collaborate, they must use a standard protocol, or collection of guidelines, for sending and receiving data packets.
There have been several protocols created. Transmission Control Protocol/Internet Protocol (TCP/IP) is one of the most commonly used protocols. Often helpful for analysing and contrasting various protocols is the Open System Interconnection (OSI) model, which is a common protocol model used in defining network communications.
The OSI Model (Open Systems Initiative)[ps2id id='The OSI Model (Open Systems Initiative)' target=''/]
The OSI model, also known as ISO/IEC 7498-1, is a standard established by the International Organization for Standardization (ISO). It's a general-purpose paradigm for talking about or explaining how computers interact through a network. At each stage, the seven-layered approach to data transfer separates the numerous activities into specific linked groups of behaviour (Fig. 1).
- Data flows down the transmit layers, over the physical link, and back up via the receive layers in the OSI model.
The data to be transmitted is sent from the transmitting computer platform to the applications layer, where it is interpreted and transferred from layer to layer down the stack, with each layer executing its own functions. The data is then sent through the network's physical layer before it reaches the target machine or another system. The data is then moved up through the layers again, with each layer executing its allocated operations before the data is used by the programme on the receiving device.
Each layer adds a header to the data during transmission that guides and identifies the packet. Encapsulation is the term for this procedure. The header and data combine to create a data packet for the next layer, which incorporates its own header and so on. After that, the merged encapsulated packet is sent and collected. The data is de-encapsulated at each layer by the receiving device, with the header details leading the operations. The data is then used for the programme. The procedure is repeated before all data has been sent and collected.
At each layer, all of the necessary and desirable operations are grouped together in a logical series. Each layer is in charge of a distinct set of tasks:
• Layer 7 – server: This layer collaborates with the application software to include the required communications functions. It verifies a communications partner's readiness as well as the services required to facilitate any data transfer. Domain name service (DNS), file transfer protocol (FTP), hypertext transfer protocol (HTTP), Internet message access protocol (IMAP), post office protocol (POP), simple mail transfer protocol (SMTP), Telenet, and terminal emulation are among the end applications it supports.
• Presentation (Layer 6): This layer verifies that the data is consistent with the communications resources. It guarantees the data formats at the device level and lower levels are compatible. It also takes care of any data formatting or code conversion that's needed, as well as compression and encryption.
• Layer 5 – session: This programme is in charge of authentication and authorization. It also maintains the link between the two communication machines, including creating, preserving, and terminating the connection. This layer ensures that the data is also delivered.
• Layer 4 – transport: This layer performs quality-of-service (QoS) functionality and assures that the data is delivered in its entirety. At this layer, data integrity is ensured by error correction and related functions.
• Layer 3 – network: The network layer is responsible for packet routing through logical addressing and switching.
• Data connection (Layer 2): Layer 2 operations bundle and unpack data in frames.
• Physical Layer 1: This layer specifies the logic levels, data rate, physical media, and data conversion functions that make up the bit stream of packets sent from one system to the next.
The OSI model has two important things to consider. First and foremost, the OSI concept is just that: a model. Although it is not needed for networking, most protocols and systems follow it closely. It's most effective for debating, explaining, and comprehending specific network functions.
Second, in certain simplified applications, not all layers are included. Although layers 1, 2, and 3 are required for some data transmission, the programme may use a special interface layer instead of the model's normal upper layers.
TCP/IP (Transmission Control Protocol/Internet Protocol)[ps2id id='TCP/IP (Transmission Control Protocol/Internet Protocol)' target=''/]
TCP/IP was created in the 1960s as part of the Advanced Research Projects Agency's (ARPA) initiative to create a national packet data network for the Department of Defense (DoD). It was first seen in colleges and government installations of UNIX-based machines. It is also the most widely adopted protocol on the Internet.
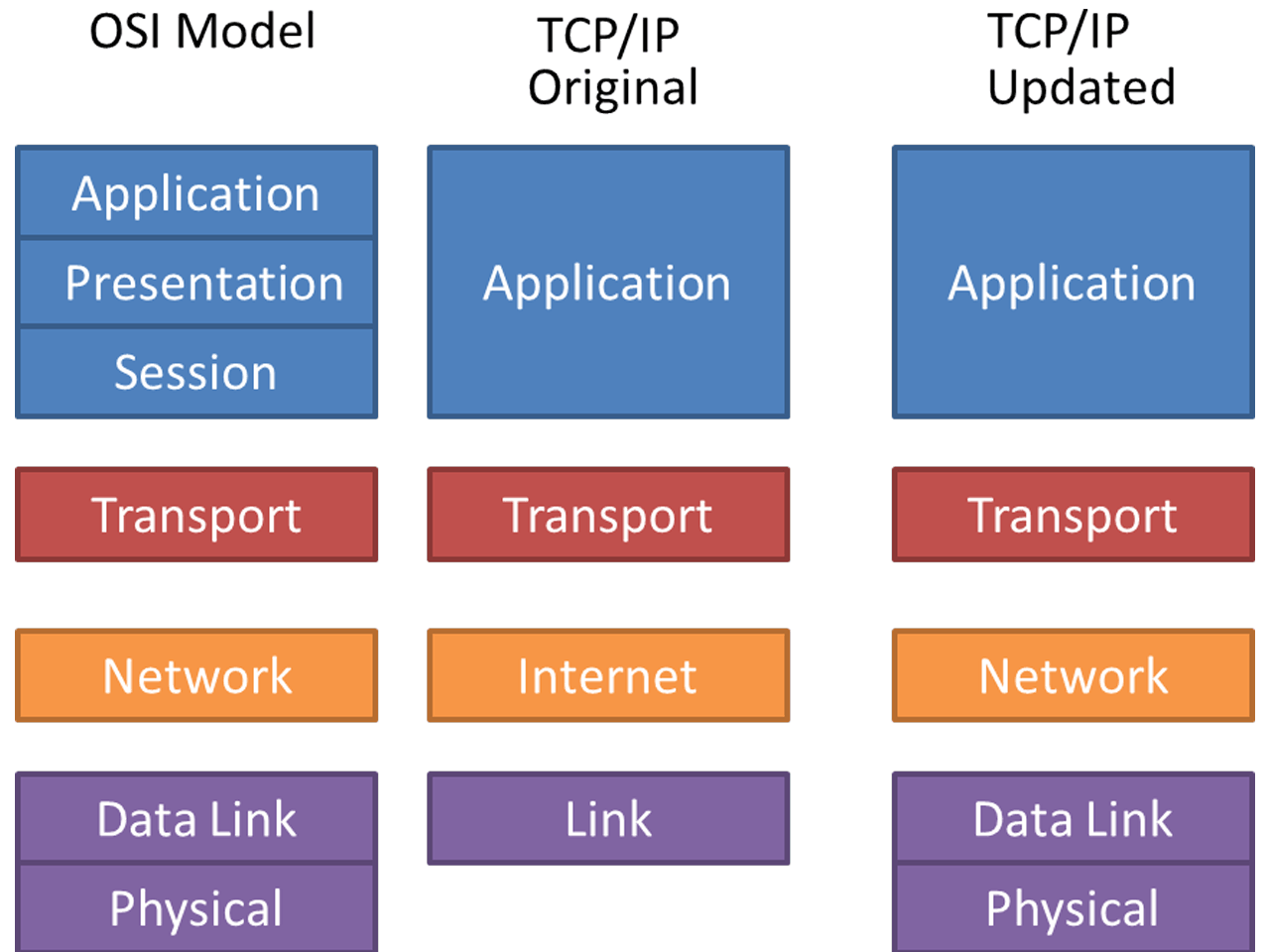
TCP/IP is a layered protocol as well, but it does not utilise any of the OSI layers, despite the fact that the layers are functionally similar (Fig. 2). Layers 1 and 2 of the OSI model are similar to the network control layer. In the OSI scheme, the Internet Protocol layer is equivalent to layer 3. Layer 4 of the OSI model is identical to the host-to-host layer. This are the TCP (transmission control protocol) and UDP (user datagram protocol) features. Finally, the framework layer is equivalent to the combination of OSI layers 5, 6, and 7.

- The OSI model's seven layers are similar to the four layers that make up the TCP/IP protocol.
The data is divided into packets by the TCP layer. Source and destination addresses, a sequence number, an acknowledgement number, a check amount for error detection and correction, and other details are all included in a header that is applied to the records (Fig. 3). The header is made up of 20 octets (each octet equals 8 bits) that are arranged in 32-bit increments. These pieces are sent from top to bottom and from left to right.

- During the encapsulation and de-encapsulation of packet data at the TCP layer, the header is inserted and then deleted.
TCP reassembles the packets in the proper sequence at the receiving end of the connection and routes them up the stack to the programme. If a mistake happens, TCP will retransmit the packet. In any scenario, TCP's primary function is to load and unpack data and have some guarantee of error-free data transmission. The TCP packet is directly transmitted by the IP layer.
The data is transmitted over the physical-layer link via the IP layer. The packet's header is added via IP (Fig. 4). The header is made up of 32 octets organised into 32-bit phrases. The 32-bit source and destination addresses should be noted. There are often seen IP addresses in dotted decimal format (e.g., 197.45.204.36), where each 8-bit octet is represented in its decimal value. The Internet Delegated Numbers Authority has assigned this address to the computer (IANA).

- During the Internet Protocol data transmission phase, the IPv4 header is used. The 32-bit source and destination addresses should be noted.
Figure 4 shows the header used in IP version 4. (IPv4). As the IANA has run out of 32-bit addresses (there are now 232! ), a newer variant is being quickly embraced. 128-bit addresses are used in IPv6 (Fig. 5). There should be enough addresses for all of the world's computers, ipads, and mobile phones, as well as all of the networks that could be linked to shape the so-called Internet of Things, with 2128 addresses (IoT).
Sites of Electronicdesign.com 2013 09 0913 Wtd Osi F5 Electronicdesign.com Files Uploads
- The Internet Protocol's current IPv6 header is identical to IPv4, but it uses 128-bit source and destination addresses.
The data is moved to the Network Access layer after the IP header has been applied. For final physical transfer, this layer repackages the data into Ethernet packets or another protocol. The Ethernet packets are then re-configured for transmission over a DSL or cable TV link, as well as over a wide-area network via Sonet or an optical transport network (OTN).
Option Application Security if you want to increase your security solutions secure your applications across multiple layers of the OSI model, from the network layer, which is protected by providers DDoS mitigation, to the application layer, which is protected by Imperva's web application firewall (WAF), bot management, and API security technology.
Online providers offers multi-layered security to safeguard applications and networks throughout the OSI stack, ensuring that websites and apps are available, readily accessible, and secure. The Provider application security solution comprises the following components:
- DDoS protection—retain uptime in all circumstances. Prevent any size DDoS assault from blocking access to your website and network infrastructure.
- CDN—With a CDN optimized for developers, you can improve website speed while lowering bandwidth expenses. Accelerate APIs and dynamic webpages by caching static resources at the edge.
- WAF—a cloud-based system that allows legal traffic while blocking malicious traffic, protecting applications at the edge. Gateway WAF protects apps and APIs inside your network.
- Bot protection—analyzes your bot traffic for abnormalities, detects harmful bot activity, and verifies it using challenge methods that do not interfere with user traffic.
- API security safeguards APIs by ensuring that only intended traffic may access your API endpoint, as well as identifying and preventing vulnerability attacks.
- Account takeover prevention detects and protects against attempts to take over users' accounts for harmful reasons using an intent-based detection method.
- RASP—protect your apps against known and zeroday threats from inside. Protection that is quick and accurate, with no signature or learning mode.
- Attack analytics—mitigate and react to actual cyber security risks with actionable information across all levels of protection in a fast and accurate manner.
What are the benefits of using the OSI model?[ps2id id='What are the benefits of using the OSI model?' target=''/]
The ISO-OSI layer model's benefits are as diverse as its structure: On the one hand, it is a good standard paradigm for computer networking—the different operating systems and other manufacturer-specific variations between networked devices are irrelevant. Both connectionless and connection-based services are available, which is a significant benefit since customers may simply utilize connectionless services, for example, when they need quicker data transmission over the internet.
The connection-based approach is still accessible and may be utilized when dependability is essential and you do not want to rely on Wi-Fi. Furthermore, OSI has a high degree of adaptability to a wide range of protocols. As a result, it is more flexible and secure than grouping all services in just one of the seven levels.
The OSI model's drawbacks[ps2id id='The OSI model's drawbacks' target=''/]
Despite the greatest potential flexibility in terms of the devices utilized, “all stakeholders” must comply to certain rules of the game in order for the OSI model to function as stated. These rules are specified in the model protocols, which may be applied to specific layers or utilized across levels. And, although the system cannot function without these protocols, they are far from well defined. Furthermore, some layers are less helpful than others:
The layer in charge of session management and the layer (Presentation) in charge of user interaction, for example, are not as helpful as other model layers. Another disadvantage is that the layers cannot operate simultaneously or independently—they are reciprocal, which means that each layer must "wait" for data from the preceding layer before it can perform its job. And this is a recurring feature throughout the model. It would not function correctly without this interaction. Furthermore, certain services are replicated on other levels (for example, the Transport Layer and the Data Link Layer (backup), but not redundantly—each with its own error control method.
In conclusion[ps2id id='In conclusion' target=''/]
TCP/IP is the older of the two data transfer protocols and is widely used around the world. The OSI paradigm, on the other hand, is a well-established principle that underpins all other data exchange protocols. It will be used as a standard for all future networking applications.
Bibliography[ps2id id='Bibliography' target=''/]
Principles of Electronic Communication Systems, 3rd edition, McGraw Hill, 2008. Frenzel, Louis E.
Andrew Russell, "The Internet That Wasn't," August 2013 issue of IEEE Spectrum
Michael Stewart, Foundational Focus: OSI Mode –Breaking Down the Seven Layers, Global Knowledge Training LLC, 2013. Stewart, Michael Stewart, Foundational Focus: OSI Mode –Breaking Down the Seven Layers, Global Knowledge Training LLC, 2013.
The TCP/IP and OSI Models, Paul Simoneau, Global Knowledge Training LLC, 2011.
If you like this content plz bookmars my website to be updated for all Tech news
https://www.techguruhub.net/2021/05/13/difference-between-tcp-ip-network/?feed_id=78401&_unique_id=62a5034ea49d5
Comments
Post a Comment