Border Gateway Protocol (BGP): What is it and how does it work?

When you're drawing a straight line on a sheet of paper, finding the right route from point A to point B is easy, but when Point A is your machine and Point B is a website halfway around the globe, things get a little more complicated.
In the latter case, the global internet's routing protocol, Border Gateway Protocol (BGP), is used to determine the best route by weighing the most recent network conditions based on reachability and routing knowledge. BGP controls how data packets are delivered between the vast networks that make up the internet which allows the internet to function as we know it.
ON THIS PAGE: Border Gateway Protocol (BGP): What is it and how does it work?
- What is the Border Gateway Protocol (BGP), and how does it work?
- Agreements on peering between autonomous systems
- What is BGP hijacking, and how does it work?
- What is the importance of IGP?
What is the Border Gateway Protocol (BGP), and how does it work?[ps2id id='What is the Border Gateway Protocol (BGP), and how does it work?' target=''/]
BGP has been dubbed "the Internet's glue" and "the Internet's postal service." BGP has been compared to GPS apps on cell phones. If you're travelling from Boston to Los Angeles, the GPS software can determine the most efficient path based on your current awareness of road conditions, traffic congestion, and whether you choose to drive on a toll road. The quickest route isn't necessarily the right path. BGP is similar to providing an ever-updated chart of the internet on which routers choose the best direction at any given moment.
The IETF defines BGP as having a primary purpose of "exchanging network reachability knowledge with other BGP schemes." When all is running well, BGP brings all disparate networks together to form the internet.
The internet has been dubbed a "network of networks" because it connects clusters of individual networks run by large organisations with other large organisations' networks. ISPs, major government departments, libraries, and research organisations are among the broad organisations that have achieved autonomous system (AS) status.
Each AS establishes its own set of rules and policies on how traffic flows across its network. Your home machine may be a member of the AS that your ISP manages, and it handles traffic to and from all other nodes in that AS. However, whenever you want to enter a site outside of the AS, BGP is invoked.
Peering agreements are agreements between AS entities that enable traffic to flow between their networks. BGP routers at the edge of AS networks advertise the IP address prefixes to which they can send traffic to their peers. These announcements are made on a regular basis through network-prefix announcements, which are used to keep each router's routing table up to date.
Agreements on peering between autonomous systems[ps2id id='Agreements on peering between autonomous systems' target=''/]
BGP routers evaluate the data they collect from prefix announcements and decide which peer is the best to submit each packet stream to at any given time using decision-making algorithms and policies defined in AS-peering agreements. The path with the fewest network hops is often chosen, but due to congestion and delay, another, longer route can potentially be quicker. The procedure repeats itself until the traffic crosses an AS and hits another BGP router attached to a separate AS, before the data reaches the AS where the destination location is located.
ISPs are used for most machines, tablets, and other gadgets to link to the internet. These access providers' networks link to larger and larger ISP networks before they have access to the internet backbone. From a starting stage, traffic is routed up the network hierarchy to the backbone, then down to the destination IP address.
(BGP may also be used for intra-AS routing, but it isn't needed since other routing protocols work just as well.) Interior Border Gateway Protocol, internal BGP (iBGP) is the name provided to it as it is used.)

Autonomous device numbers (ASNs) are used by network operators to monitor routing within their own networks and to share routing details with other ISPs. The Internet Allocated Numbers Authority (IANA) assigns these numbers, which are then transmitted to ISPs and other network providers by regional internet registries. An ASN contains both 16-bit (two-byte) and 32-bit (four-byte) numbers, similar to an IP address. There are about 100,000 ASNs worldwide as of January 2021, with around 29% of them in the United States.
What is BGP hijacking, and how does it work?[ps2id id='What is BGP hijacking, and how does it work?' target=''/]
The number of BGP ads grows as new ASNs enter the Internet to have new routes for traffic, generating a larger and larger attack surface. BGP hijacking is an issue caused by the assumption that each AS is telling the truth about the IP addresses it owns and the routing details it shares.
Adversaries hack BGP routing tables in this assault to make a compromised router advertise prefixes that aren't allocated to it. If such misleading commercials claim that a better route exists than the legitimate path, traffic can be diverted there—only to be led to fraudulent servers that capture passwords, download malware, and carry out other harmful activities. Meanwhile, end users believe they are accessing official websites.
In 2018, a Russian ISP wrongly declared a set of IP prefixes that supposedly belonged to a collection of Amazon DNS servers, resulting in a high-profile case of BGP hijacking. Users who tried to log in to a cryptocurrency website were routed to a fake site, where hackers stole around $152,000 in cryptocurrency.
In another well-documented incident, Pakistan Telecom tried to censor YouTube in 2008 as an ISP by selling its own BGP routes to the web, preventing users from accessing it. The latest pathways, on the other hand, were revealed to the ISP's upstream providers, who then broadcast them to the rest of the Internet. As a result, Web requests for YouTube were routed via Pakistan Telecom, resulting in a huge blackout for the network as well as a server overload for the ISP.
How to Defend Against BGP Hijacking
The use of IP address-prefix filtering, which prevents inbound network traffic from networks known to be dominated by malicious actors, is one strategy for defending against BGP hijacking. Another is BGP hijack-detection tracking, which checks for unusually high latency, poor network capacity, or misdirected Internet traffic, both of which may indicate hijacking attempts.
BGPsec is a protocol for encrypting data
BGPsec is a protection extension that uses cryptographic authentication for advertised routes and allows backbone routers to sign their route-update advertisements with digital signatures. Unauthorized attackers would have a harder time advertising poor routes for ASes, as well as preventing misconfigurations. However, to put this into action, the whole internet will have to follow it at the same time. Imagine declaring that the whole internet would be unavailable for 10 minutes in order to upgrade itself. You can imagine how well that will go down.
Nonetheless, there is reason to be optimistic. A task force called Mutually Agreed Norms for Routing Security (MANRS) was established in September 2020 to assist content-delivery networks and other cloud providers in implementing filters and cryptography to protect BGP. The organisation, which was founded in 2014, seeks to “commit to the baseline of routing protection identified by a collection of six security-enhancing measures, five of which are necessary to implement.”
The acts are as follows:
- Prevent erroneous routing knowledge from spreading.
- Prevent traffic from coming from IP addresses that aren't valid.
- Global organisational cooperation and planning can be made easier.
- Validation of routing details on a global basis can be made easier.
- Encourage others to use MANRS.
- Provide peering members with tracking and debugging software (optional).
The routing public key infrastructure (RPKI), a public archive of routes that have been cryptographically signed to show their trustworthiness, is being promoted by MANRS. Although RPKI users post their routes and search the database to validate others' routes, the framework will only prevent leaks and outages if everybody uses it. Otherwise, BGP routers would be required to tolerate unvalidated ads in order to maintain the internet going.
Another company is using collective shame to attempt to persuade businesses to help RPKI. Users can get alerts on ISPs that are enforcing RPKI and read a FAQ on the situation at Cloudflare's website "Is BGP Safe Yet?" More specifically, they may use a button to determine whether or not their ISP is safe.
Although this platform may seem to be a marketing ploy, its presence highlights the problem's continuing severity.
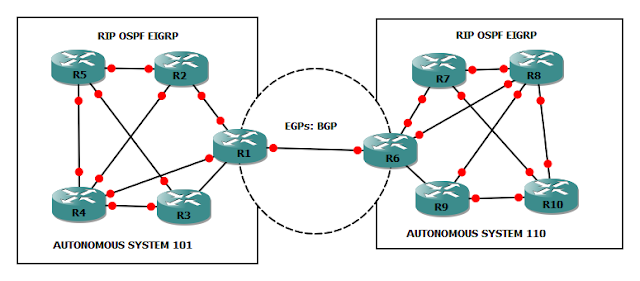
BGP's full name is the Border Gateway Protocol, and its Chinese equivalent is the Border Gateway Protocol. The name is more abstract, and I believe the wiki Chinese explanation is preferable (the wiki English does not even have a similar explanation). BGP is the Internet's primary decentralized autonomous routing system. According to this description, this is a routing protocol for the Internet. Its status is core (it is presently the most essential and only routing protocol used on the Internet), and its goal is to decentralize in order to achieve different levels of network autonomy.
But isn't it still a little hazy? Let's have a look at some similar ideas: AS (Autonomous system): This is an abbreviation for Autonomous System. An autonomous system including all IP networks and routers under the authority of one (or more) organizations that enforce a single routing policy for the Internet. That is, an AS is a self-contained overall network for the Internet. BGP-enabled network autonomy also refers as AS autonomy.
Each AS is assigned a unique number. IGP (Internal Gateway Protocol): An internal gateway protocol, often known as a routing protocol, that is used inside an AS. Different routers inside an AS may also handle multiple networks. Routing information is needed between each router in order to determine the reachability of the sub-network. These routes are managed using IGP. RIP and OSPF are two examples of representative implementations.
EGP (Exterior Gateway Protocol): A routing protocol used between many ASs that has since been phased out and replaced with BGP. BGP has the same status as EGP since it was designed to replace it. However, BGP may also be used inside an AS. As a result, BGP is further subdivided into IBGP (Interior BGP: connections between the same AS) and EBGP (Exterior BGP: BGP connection between different ASs). The presence of EBGP is more known now that EGP has been superseded, but the IGP protocol is still alive and well (in this case, OSPF).
What is the importance of IGP?[ps2id id='What is the importance of IGP?' target=''/]
The IGP protocol is intended for use in the same AS network. Because the size of an autonomous network is usually modest, the design of a large-scale network is not taken into account. OSPF has a speed barrier when an autonomous network is big enough (described later). BGP is intended to function on the Internet.
Because it is intended to suit the needs of big networks, IBGP may be utilized inside large private IP networks. In general, these routing protocols are IGP for small-scale private networks, IBGP for large-scale private networks, and EBGP for the Internet. Why do you need BGP? BGP claims to be the protocol that allows the Internet to function. It seems to be crucial. Why is it that there is so little touch in everyday life? There seems to be no mention of BGP in the cloud. Let's look at the causes behind this.
Assume you're creating a cloud environment that offers virtual machine services. Because the virtual machine in the cloud requires Internet connection, you apply to the ISP (Internet service provider) for a public network IP address, where the ISP may be Unicom, mobile, telecommunications, and so on. Virtual machines may use the router's NAT/PAT (Network / Port address translation) to convert their private IP to this public IP, and then you specify the address of the ISP router as the default route on the cloud router.
Following address translation, IP packets are transmitted to the ISP and then to the Internet (this is also the principle that our home router can make the home device online). As a result, your version 1.0 cloud is simply live. BGP isn't required here. What should I do once the updated version is available? Of course, the next edition is being worked on! The following form of the requirement is to get access to virtual machines over the Internet (that is, accessing our home computers from the Internet). This is a simple task. Port forwarding may be used to map a virtual machine's port to a public network IP port.
For example, if the virtual machine's 22 port is mapped to the public network IP's 1122 port, you may log in to the virtual machine using Internet ssh to the public network IP: 1122. This portion of the job is still done in your cloud's router. As a result, your version 2.0 cloud is operational, and you no longer need BGP. Version 2.0 allows Internet connectivity to virtual computers, however there are still issues: For each open port, each virtual machine must be mapped once. The number of IP ports available on public networks is restricted.
To resolve these issues, you applied to Unicom for certain public IP numbers and allocated virtual network IP addresses to virtual machines that need external network connectivity. So your version 3.0 cloud is up and running, and you still don't need BGP. because: Unicom is the only ISP that is linked to your cloud. China Unicom is the sole provider of Internet connectivity.
As a result, the default route of your cloud router may only be configured to the address of the ISP router. China Unicom assigns the public IP address in your cloud. Unicom is well aware of which IP address to use as the next hop in order to get access to those IP addresses. After all, Unicom's IP address is restricted, and China Unicom is still disconnected.
This is available in three different forms. First, you applied to the IANA for your own public IP pool (Internet Assigned Numbers Authority). Because you have your own public IP address, you should consider requesting for an AS number as well. The AS number is a 16-bit number that is shared by over 60,000 numbers across the globe. 1 – 64511 is the only one in the world, and 64512 – 65535, like the private network section, is self-contained. Each autonomous network must get its own AS number. China Unicom's AS number is 9800.
Then you purchased the connection independently from China Unicom and Telecom, so you can use telecommunications even if Unicom is down. The issue now is, how does China Unicom or Telecom know what IP address you are requesting? In other words, now that I've called Unicom broadband, how can I reach the public IP address of your cloud? · Is your cloud router's default route set to Unicom's ISP router or telecommunications?
Finally, you must utilize BGP on your cloud 4.0 version. You may transmit routing information from your own cloud to China Unicom and Telecom through BGP, so that ISPs know how to reach Xiao Ming's public network virtual machine, allowing our regular users to connect to your network via ISP. However, by deploying BGP services in the cloud, you may modify the default routes for cloud routers.
BGP roles include:
- Because it is a PVP, BGP communicates the entire autonomous system/network path topology to other networks
- Maintains its routing table with topologies of all externally connected networks
- Supports classless interdomain routing (CIDR), which allocates Internet Protocol (IP) addresses to connected Internet devices
When used to facilitate communication between different autonomous systems, BGP is referred to as External BGP (EBGP). When used at host networks/autonomous systems, BGP is referred to as Internal BGP (IBGP).
BGP was created to extend and replace Exterior Gateway Protocol (EGP).
Comments
Post a Comment