Attacks, Detection, And Prevention: What You Need To Know About ARP Spoofing

Spoofing is described as imitating (something) while exaggerating its distinguishing characteristics for comedic impact. Spoofing is a widespread activity by infamous users to steal data and traffic intended for a specific person, not just in the physical world but also in the computer networking world.
Despite the fact that there are many spoofing attacks known in the computer network universe, DNS spoofing, IP spoofing, MAC spoofing, and even ARP spoofing are several of the most well-known spoofing attacks that are familiar to almost all of us, even though we have no awareness of computer networks.
Attacks Using ARP Spoof Allows hackers to impersonate your computer and steal all of your traffic
It's a frequent plot device in espionage films. You're pleasantly watching with your popcorn in hand when a character does something totally unexpected and out of character. You're taken aback. You think to yourself, "What just happened?" I thought they were both nice people? “Why did he shoot the other guy?” Then comes the narrative twist: the evil man was wearing a mask the whole time and impersonating someone else to accomplish his malicious objectives! However, in the realm of cybersecurity, the “bad man in a disguise” is a perfect example of how ARP attacks operate.
When an attacker manipulates the relationship between Media Access Control (MAC) addresses and Internet Protocol (IP) addresses, this is known as ARP spoofing. As a consequence, they seem to all other devices on your network to be someone else (and thus they receive all the traffic meant for the real user). The consequences may be serious, since ARP attacks can result in not just data theft, but also session hijacking, distributed denial of service (DDoS) assaults, and more.
So, first and foremost, what is ARP? What is the process of ARP? How do you know whether it's there? And, most importantly, how can it be avoided?
Let's talk about it.
ARP Preview News
Attacks on ARP Allows hackers to impersonate your computer and steal all of your data.
It's a typical plot device in spy films. You're happily enjoying with your popcorn in hand when a character does something totally out of character. You're taken aback. “What just happened?” you ponder. Isn't it true that they're still decent guys? “What was he thinking as he shot the other guy?” There comes the plot twist: the evil man was wearing a disguise the entire time and impersonating someone else to fulfil his sinister ends!
However, in the field of cryptography, the “bad guy in a disguise” is a perfect example of how ARP spoofing attacks operate.
When an intruder manipulates the connection between Media Access Control (MAC) addresses and Internet Protocol (IP) addresses, this is known as ARP spoofing. The end effect is that they seem to all those devices in the network to be someone else (and thus they receive all the traffic meant for the real user). The consequences can be serious, as ARP spoofing attacks can result in data stealing, session hijacking, distributed denial of service (DDoS) attacks, and more.
So, first and foremost, what is ARP? What is ARP spoofing and how does it work? How do you tell if it's there? And, most specifically, what would you do to avoid it?
Let's talk about it.
What exactly is ARP?
To truly grasp what ARP spoofing is and how it functions, we must first comprehend what ARP is. The primary feature of the Address Resolution Protocol is to resolve internet layer addresses into connection layer addresses. Another way of thinking of ARP is that it converts MAC addresses to IP addresses (and vice-versa).
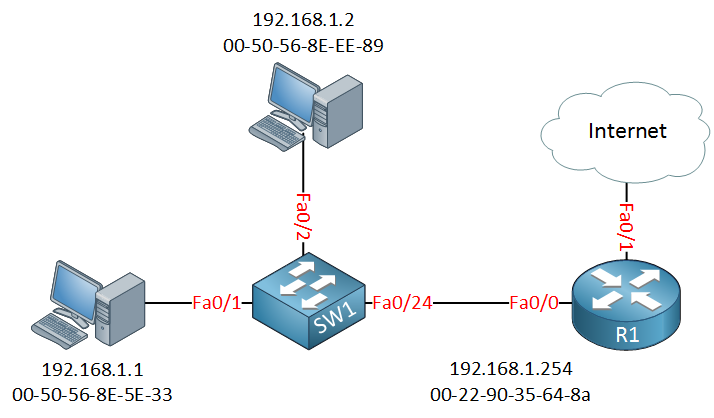
ARP is the method by which your computers communicate with the router or gateway and, as a result, link to the internet. When an IP packet is transmitted between hosts on a local network, the mapping table, often known as an ARP cache, is accessed. It's essentially a cross-reference between MAC addresses and IP addresses that allows users to link to various network destinations.
If the host does not recognise the MAC address of a specific IP, a broadcast packet is sent (also referred to as an ARP request). The computer whose IP address was included in the ARP request responds with its MAC address. So, in case there are any further queries from the same computer, it is connected to the ARP cache.
ARP's security
Regrettably, ARP was not designed with protection in mind. ARP is also a stateless protocol, which means that even though an ARP request is never received, hosts can archive ARP responses. When a fresh ARP reply is sent, any ARP entries that haven't expired are overwritten.
Most significantly, no authentication is done to ensure that an ARP request comes from an authorised person. ARP spoofing attacks are possible because of this flaw in ARP.
ARP will only be used for IPv4 and 32-bit IP addresses. In the other side, IPv6 fixes some of the protection problems that ARP has. Instead, it implements the Neighbor Discovery Protocol (NDP), which utilises cryptographic keys to verify the presence of hosts. However, since the rest of the internet only uses IPv4, ARP is still commonly used.
What is ARP Spoofing, and how does it work?
When malicious ARP packets are submitted to a LAN's default gateway, ARP spoofing, also known as ARP poisoning, happens. This is required to adjust the ARP table's IP/MAC address pairings. The hacker instructs the gateway that their MAC address can now be linked to the IP address of the target victim. The attacker's IP address is compared to the target's MAC address, and vice versa.
The default gateway then caches the latest IP/MAC relationships and transfers them to the rest of the network's computers. This ensures that instead of going to the expected receiver, any future messages would go to the attacker's computer first.
ARP spoofing attacks are carried out at a low stage, which helps the hackers because it is impossible for victims to notice that their traffic has been tampered with (though, as we'll see shortly, there are ways to both detect and avoid ARP spoofing attacks).
An ARP Spoofing Attack's Steps
Attacks on ARP spoofing typically pursue the same pattern:
- After gaining entry to the local network, the intruder searches it for IP addresses of devices.
- To forge ARP answers, the intruder uses a spoofing technique like Driftnet or Arpspoof.
- The IP address of the tool is set to fit the victim's IP subnet.
- The perpetrator's MAC address is combined with the victim's IP address in ARP packets, causing the router and PC to bind to the attacker instead of each other.
- As a result, the ARP cache is updated, and the PC and router continue to communicate with the intruder.
- Other hosts can now relay data to the attacker regardless of the attacker seeing the spoofed ARP cache entries.
In the illustration below, you can see how both of the elements come together:

Diagram on ARP Spoofing
What Types of ARP Spoofing Are There? For this purpose,
A big part of what makes ARP spoofing so risky is that it's often used as a springboard for more complex assaults. After successfully executing an ARP spoofing assault, an intruder will quickly switch to:
- DDoS attacks – In order to execute a DDoS assault, the intruder should use the address of the server they want to attack instead of their own MAC address. The victim would be flooded by traffic if this is repeated over a significant number of IP addresses.
- User hijacking – Using ARP spoofing, an intruder can obtain the session ID and use it to gain entry to accounts that the target is logging into.
- Continued packet stealing – The perpetrator isn't required to take any additional action. They will continue sniffing your packets and stealing your data (which is why, as we'll see later, using TLS and HTTPS to encrypt your communications is so important).
- Man-in-the-middle assault – This will be a man-in-the-middle attack. The intruder will intercept and modify traffic as well as send malicious files or websites to the victim's computer.
How can you tell if anyone is spoofing your ARP?
For detecting ARP spoofing assaults, there are a few different options available. First and foremost, there are third-party device applications. There are two types of this. First, there are more general networking tools, such as Wireshark (also free and open source), that enable you to display all of your network traffic and aid in troubleshooting and analysis. Then there are programmes like XArp (free and paid models available) that are designed specifically to detect ARP spoofing and actively scan the network for ARP spoofing assaults.
Can you choose not to instal a third-party programme? And you're in luck, so you can use the operating system's built-in features to detect ARP spoofing. We'll look at how to do it on Windows and Linux in this article (the commands are the same on both):
- Since this approach relies on the command line, we'll start by logging in as an administrator to an operating system shell. It would appear like this in Windows 10:

To see the ARP chart, type the following command:
-a arp
The end product should resemble the following:
- Next, see whether there are any IP addresses of the same MAC address (referred to as "Physical Address" above). This is the telltale sign that an ARP spoofing assault is underway.
We are, thankfully, healthy. However, if an assault were to take place, it would resemble the image below. The smoking gun is the duplicate MAC addresses belonging to two separate IP addresses (circled in red):
Since the router's IP address is most definitely 192.168.43.1 in the case above, it's fair to say the attacker's IP address is 192.168.43.220.
The command prompt process is more cumbersome and challenging to utilise while you're working with a vast network since you'll have to check tens, hundreds, or even thousands of entries (as compared to only a few if you're on your home network, for example). In that scenario, advanced programmes like Wireshark or XArp, such as those we listed earlier, are usually your best choice for detecting ARP spoofing.
How to Protect Yourself from ARP Spoofing
There are many steps the company may do to reduce the likelihood of an ARP spoofing assault on your network. Some of them are particular steps you can perform, and others are common best practises that can be practised at all times:
- To better detect tainted ARP packets, use packet filtering. It operates by determining if the packets contain contradictory source details and, if so, preventing them from reaching other users.
- Avoid confidence relationships where authentication is based on IP addresses. As a result, attackers can easily carry out ARP spoofing assaults.
- Use a Virtual Private Network (VPN) – VPNs encrypt all of your communications, rendering your traffic useless to any intruder trying to spoof your ARP. However, as the network grows in complexity, this becomes less possible since each device and server must have its own VPN link (resulting in a negative performance hit for your network).
- Use Static ARP – ARP allows for the development of static entries for every IP address. You can block anyone from listening in on ARP responses for that address by utilising a static ARP entry. If a computer connects to a router on a regular basis, for example, you should define a static ARP entry for the router to avoid ARP spoofing attacks.
- Encrypt data in transit using cryptographic network protocols like Transport Layer Security (TLS), Protected Shell (SSH), or secure HTTP (HTTPS).
- Using ARP spoofing detection programme to detect assaults, as we covered in the previous segment. They work by checking and verifying data until it is sent out, as well as blocking data from spoofed outlets. Other common resources include Arpwatch, which can be found here, and ARP-Guard, in addition to XArp.
- Through tracking address resolution, intrusion-detection tools like Snort can help avoid ARP spoofing assaults.
- Finally, once you've been through the rest of this checklist, simulate a real spoofing assault and see if your defences are up to par. If the assault succeeds, identify the vulnerable points and fix them.
The Invisible Man's Location (or Woman)
ARP spoofing threats can be tough to spot if you don't know what to check for. When you think about it, that's just what an intruder is doing – they're impersonating a specific computer on the network and using their invisibility to intercept data they shouldn't have. ARP spoofing, as we've seen, will contribute to further assaults, which can spell tragedy for your business.
Ensure that your employees are mindful of ARP spoofing and the threats it presents, and that you have resources in place to track those assaults on your network. The unseen attackers won't be able to hide any longer, and your data will be secure.

More Tips & Tricks about ARP
Detection and prevention of ARP spoofing
It's not as though these nefarious acts can't be stopped. Here are some of the techniques used to identify and defend against ARP spoofing:
Data Encoding and Authentication
Authenticating the identity of a data sender in any form will help you avoid collecting data from a malicious recipient. To authenticate users, authentication uses passwords from both schemes.
Furthermore, the data is protected by the sender using certain keys before being sent to the receiver. The encrypted data can only be decoded using certain keys that the sender has already exchanged with the recipient. These features, especially encryption and decryption, are part of network protection.
Filters with packets
Packet filters are similar to inspectors in that they sit and closely analyse all packets sent through the network. Packet filters are often used with firewall applications, and they maintain an eye out for harmful packets.
A malicious packet, for example, may include packets from outside the network with source addresses from within the network, and vice versa.
Using ARP Static
This is a more traditional method, but it works well. You manually configure a preset ARP for your subnetwork machines to eliminate the possibility of changes. However, on a big network, it is not advised since there would be a number of static ARPs, and any minor modifications would be too much hassle for the network administrator.
Using VPNs (Virtual Private Networks) VPNs (Virtual Private Networks) are one of the safest ways to defend yourself from ARP spoofing attacks (here are some best VPNs). Not only does a Virtual Private Network use an encrypted tunnel for data transfer, but it often encrypts the data that passes via it.
Using Anti-ARP Software
The majority of the methods listed above, such as the Static ARP methodology, either involve expenditure or are not absolutely failsafe. It can only defend against basic ARP assaults. Anti-ARP techniques are one method that network administrators propose for identifying and stopping the intruder.
Here's a quick puzzle for you to complete:
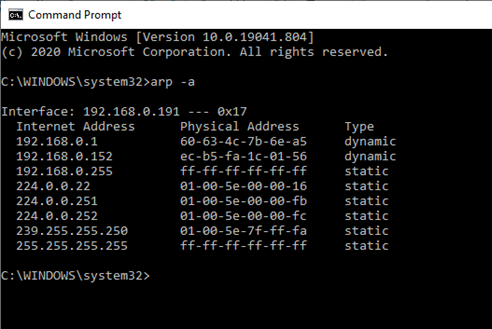
Below is a snapshot of my computer. I discovered it by using the “arp -a” command. Can you tell me what's wrong with the ARP table below based on what you've read?
CMD is used to track ARP spoofing.
Here's a clue: Keep an eye out for duplicates. Will you now address the following questions based on your findings?
Comments
Post a Comment