What is Dynamic Multipoint VPN? DMVPN Configuration

Many people who use networked connections that may include transmitting and receiving sensitive data are familiar with VPNs (or Virtual Private Networks). Dynamic Multiple VPN, such as Cisco DMVPN, encrypts transmitted data in the same way that a traditional VPN does. They do so, however, in a manner that ensures the security of communications between branch offices in particular. It does this with a centralised design that makes deployments across the whole IT scope of the company easy to execute and maintain.
What exactly is DMVPN?
DMVPN Cisco is, in essence, a solution that enables multiple branch sites sharing the same resources to interact directly and securely with one another through public WAN or internet connections rather than an internal network. It does this by using a centralised architecture that can apply VPN protection and granular access restrictions on an as-needed basis, rather than relying on a persistent VPN connection between the multiple sites. As a result, when communications are open or access to certain digital resources is required, it employs VPN security measures more selectively. DVPN also incorporates means of communication, such as VoIP, with the VPN's security.
DMVPN Advantages
There are a number of advantages to adopting DMVPN over a permanent VPN or, in the case of DMVPN versus MPLS networks, DMVPN versus MPLS networks. The following are some of the most often mentioned advantages:
In general, it provides higher internet speed and stability.
By combining VPN with communication techniques, the cost of secure communications and connections between branches is reduced.
Through a centralised system, easier branch-to-branch communications and linkages are possible.
By protecting routing using IPsec technology, the chance of downtime is reduced.
DMVPN enables data transfers over a secure network without the need for a VPN server or router at headquarters. While a VPN serves as a link between distant locations and headquarters or between branches, the DMVPN develops a mesh VPN protocol that may be deployed selectively to existing business connections. Each location (or spoke) may safely link to one another. This is accomplished through VPN firewall concentrators and routers, as well as DMVPN settings on routers at distant locations, allowing the DMVPN mesh to be applied to the connection being made at the moment.
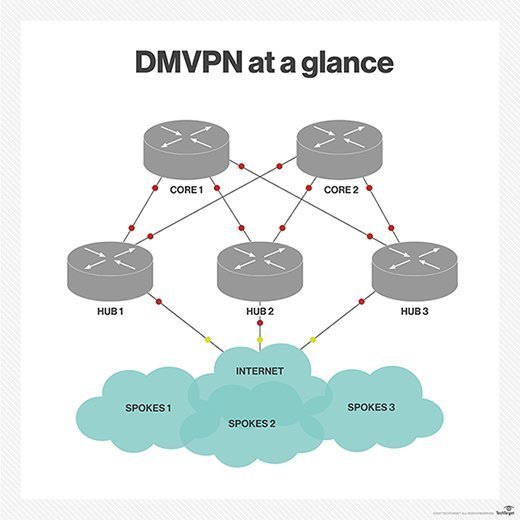
Getting a Glimpse of Dynamic Multipoint VPN (DMVPN)
Components of DMVPN
Many GRE tunnel interfaces: a single GRE interface may protect multiple IPsec tunnels, decreasing the DMVPN configuration's total scope.
IPsec tunnel endpoint discovery: no need to setup static crypto maps between specific IPsec tunnel endpoints.
Routing Protocols: which may greatly improve the DMVPN's ability to discover routes between distinct destinations.
NHRP: This protocol allows for the deployment of spokes with allocated IP addresses, which can subsequently be linked to from the central DMVPN hub.
Phases of the DMVPN
DMVPN design may be broken down into three basic categories, or phrases, all of which can be found in the Cisco DMVPN design reference. However, to describe them succinctly, they are as follows:
HUB-and-spoke tunnel deployment is used in DMVPN Phase 1. Inter-branch connections are established exclusively via the central DMVPN hub and the individual spokes, similar to how a regular VPN system works.
DMPVN Phase 2 employs spoke-to-spoke tunnel deployment, which eliminates the need for data to initially go to a central hub as long as precise routes for the spoke subnets are in place.
DMPVN Phase 3 enables for spoke-to-spoke tunnel deployment without the need for particular pre-made routes, instead relying on NHRP traffic indicator signals from the hub to secure pathways on the fly.
Network Architecture with Hubs and Spokes
The Hub and Spoke Network Architecture, as previously stated, is a method of effectively managing the endpoints that are being protected. There are three stages, each of which is appropriate for various configurations. In general, the hub is used to set the protocols that secure the connections, and these protocols are subsequently applied to the network's spokes (or endpoints). This system may be centralised to require spoke-to-spoke tunnels to pass through the hub first, or it may be decentralised to eliminate the hub completely.
Dynamic Multiple VPN is a complicated issue, but it's a security configuration that may help enterprises who employ a lot of distant endpoints (or flexible endpoints that move around a lot) maintain their network secure while keeping it adaptable and affordable.
DMVPN is a good option for creating dynamic secure overlay networks. The following technologies are combined:
- Multipoint GRE (mGRE)
- Next-Hop Resolution Protocol (NHRP)
- Dynamic Routing Protocol (EIGRP, RIP, OSPF, BGP)
- Dynamic IPsec encryption
- Cisco Express Forwarding (CEF)
I'd want to sketch out the network first. Two distant sites (SPOKE) and a central headquarters will be setup in the DMVPN (HUB). The two distant sites will have a spoke-to-spoke link and will be linked to the central headquarters.

Step 1: Set up the Cisco DMVPN Hub
Create the mGRE tunnel interfaces once you've setup your router's LAN and WAN interfaces.
interface FastEthernet0/0
description LAN-Network
ip address 192.168.1.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
description WAN-Network
ip address 1.1.1.10 255.255.255.0
duplex auto
speed auto
After that, configure the Tunnel0 interface. Important elements are highlighted in bold (they are what make the change different from a typical tunnel interface configuration). If you're acquainted with GRE tunnels, you'll see that tunnel destination has been substituted with tunnel mode gre multipoint, indicating that this is a multipoint GRE tunnel.
interface Tunnel0
description mGRE - DMVPN Tunnel
ip address 172.16.0.1 255.255.255.0
no ip redirects
ip nhrp authentication firewall
ip nhrp map multicast dynamic
ip nhrp network-id 1
tunnel source 1.1.1.10
tunnel mode gre multipoint
Configure Cisco DMVPN Remote 2 and Remote 3 in Step 2.
We need to setup the two distant routers now that we've established the HUB.
Configuring Remote 2
First, we must setup the LAN and WAN interfaces.
interface FastEthernet0/0
description LAN-Network
ip address 192.168.2.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
description WAN-Network
ip address 2.2.2.10 255.255.255.0
duplex auto
speed auto
Configure the tunnel now.
interface Tunnel0
description R2 mGRE - DMVPN Tunnel
ip address 172.16.0.2 255.255.255.0
no ip redirects
ip nhrp authentication firewall
ip nhrp map multicast dynamic
ip nhrp map 172.16.0.1 1.1.1.10
ip nhrp map multicast 1.1.1.10
ip nhrp network-id 1
ip nhrp nhs 172.16.0.1
tunnel source FastEthernet0/1
tunnel mode gre multipoint
Setting up Remote 3
Configure your LAN and WAN interfaces.
interface FastEthernet0/0
description LAN-Network
ip address 192.168.3.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
description WAN-Network
ip address 3.3.3.10 255.255.255.0
duplex auto
speed auto
Then set up the tunnel.
interface Tunnel0
description R3 mGRE - DMVPN Tunnel
ip address 172.16.0.3 255.255.255.0
no ip redirects
ip nhrp authentication firewall
ip nhrp map multicast dynamic
ip nhrp map 172.16.0.1 1.1.1.10
ip nhrp map multicast 1.1.1.10
ip nhrp network-id 1
ip nhrp nhs 172.16.0.1
tunnel source FastEthernet0/1
tunnel mode gre multipoint
IPSec Configuration (Step 3)
We must use IPSec to protect the traffic (i.e., to guarantee that it is not conveyed in plain text).
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
!
crypto isakmp key plixer address 0.0.0.0
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
crypto ipsec profile protect-gre
set security-association lifetime seconds 86400
set transform-set TS
!
interface Tunnel 0
tunnel protection ipsec profile protect-gre
Note that while utilising dynamic IP addresses, you must use 0.0.0.0 0.0.0.0.
Remote 2 and Remote 3
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
!
crypto isakmp key firewall.cx address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
crypto ipsec profile protect-gre
set security-association lifetime seconds 86400
set transform-set TS
!
interface Tunnel 0
tunnel protection ipsec profile protect-gre
The isakmp peer address is again 0.0.0.0 0.0.0.0. Despite the fact that the hub's public IP address is known, R2 and R3 may create a dynamic VPN tunnel between them. Because their public IP address changes often, it's critical to utilise 0.0.0.0 0.0.0.0 for the remote peer.
To test that the IPSec setup is working, use the command display crypto session.
Step 4: Establishing a connection between DMVPN and mGRE
The last step is to turn on routing in the DMVPN network.
HUB
ip route 192.168.2.0 255.255.255.0 172.16.0.2
ip route 192.168.3.0 255.255.255.0 172.16.0.3
Remote 2
ip route 192.168.1.0 255.255.255.0 172.16.0.1
ip route 192.168.3.0 255.255.255.0 172.16.0.3
Remote 3
ip route 192.168.1.0 255.255.255.0 172.16.0.1 ip route 192.168.2.0 255.255.255.0 172.16.0.2
That's all there is to it! Your DMVPN network has been successfully setup. On the router, type display dmvpn to see whether it's working.
Comments
Post a Comment